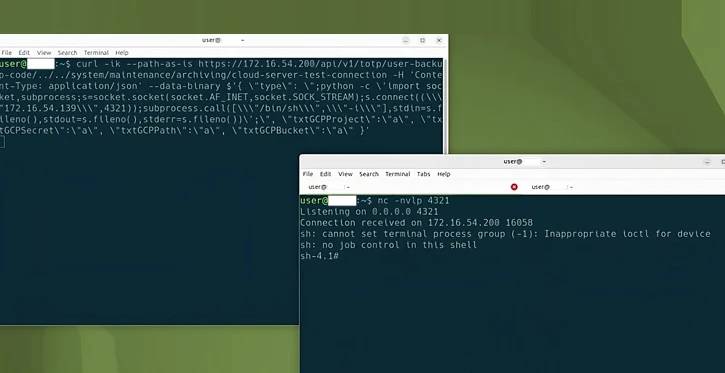
Ivanti Gateway Vulnerabilities Are Being Actively Exploited, Alert Five Eyes Agencies
The cybersecurity advisory, which highlights that the Integrity Checker Tool (ICT) can be tricked into giving a false sense of security, was released by the Five Eyes (FVEY) intelligence alliance. Cyber threat actors are known to be taking advantage of security flaws in Ivanti Connect Secure and Ivanti Policy Secure gateways.
“Ivanti ICT is not sufficient to detect compromise and that a cyber threat actor may be able to gain root-level persistence despite issuing factory resets,” the agencies said.
Since January 10, 2024, Ivanti has revealed five security flaws affecting their products; of these, four are now being actively exploited by several threat actors to spread malware.
CVE-2023-46805 (CVSS score: 8.2) – Authentication bypass vulnerability in web component
CVE-2024-21887 (CVSS score: 9.1) – Command injection vulnerability in web component
CVE-2024-21888 (CVSS score: 8.8) – Privilege escalation vulnerability in web component
CVE-2024-21893 (CVSS score: 8.2) – SSRF vulnerability in the SAML component
CVE-2024-22024 (CVSS score: 8.3) – XXE vulnerability in the SAML component
In a report released last week, Mandiant detailed how a malware variant known as BUSHWALK is encrypted and stored in a directory that ICT has blocked at /data/runtime/cockpit/diskAnalysis.
This month, Eclypsium also brought attention to the directory exclusions, claiming that the program omits a dozen directories from scanning and enables an attacker to obstruct the integrity check while still leaving backdoors in place in one of these pathways.
Agencies from Australia, Canada, New Zealand, the U.K., and the U.S. said that “the safest course of action for network defenders is to assume a sophisticated threat actor may deploy rootkit level persistence on a device that has been reset and lay dormant for an arbitrary amount of time.”
They also recommended that companies “consider the significant risk of adversary access to, and persistence on, Ivanti Connect Secure and Ivanti Policy Secure gateways when determining whether to continue operating these devices in an enterprise environment.”
According to data released by online security provider Akamai, over 1,000 clients are the subject of almost 250,000 exploitation attempts that are identified every day from over 3,300 distinct attacker IP addresses spread across 18 different countries.
“Most of these attack attempts were probes aimed at delivering a payload that serves as a proof-of-concept (PoC) for successful remote command execution by sending a beacon request to an attacker-controlled domain,” according to Noam Atias and Sam Tinklenberg.
In response to the alert, Ivanti said that it is not aware of any cases in which threat actors have successfully persisted after factory resets and security upgrades have been applied. Additionally, a new version of ICT is being released, which according to the company, “provides additional visibility into a customer’s appliance and all files that are present on the system.”



