According to documents, Facebook may have used user devices to eavesdrop on competitors.
According to a new set of unsealed court documents, Facebook initiated a covert initiative in 2016 with the intention of obtaining, deciphering, transferring, and utilizing encrypted private in-app analytics provided by Amazon, Snapchat, and YouTube. Plaintiffs claim that the Mark Zuckerberg-owned technology conglomerate considered paying adolescents to install “kits” on their devices.
Facebook used an SSL man-in-the-middle cyberattack method to intercept and decrypt the analytics traffic of Snapchat, YouTube, and Amazon.
The initiative, codenamed “Ghostbusters,” despite internal opposition, sought to intercept the encrypted app traffic of competitors for analytics purposes. Probably illegal and “potentially criminal,” according to advertisers who are suing Meta, this practice violates wiretapping laws.
Facebook developed unauthorized access-decrypting “kits,” which were custom technologies installed on iOS and Android devices to impersonate official servers and decrypt traffic. Facebook utilized the information to strategize competitive attacks against Snapchat and other firms.
A novel phishing attack conceals a keylogger within a bank payment notification.
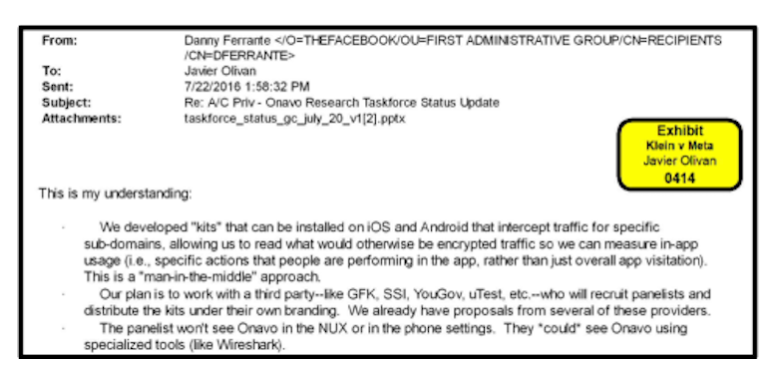
“We have created “kits” that are compatible with iOS and Android platforms. These kits intercept traffic intended for particular sub-domains, enabling us to decrypt otherwise encrypted data and measure in-app usage (i.e., specific actions performed within the app as opposed to overall app visitation).” This is a “man-in-the-middle” strategy,” reads the internal correspondence that was disclosed in the court document.
Additionally, the strategy was comprehensive: procure panelists through intermediaries and disseminate the “kits” bearing their own logo. Secret kits were undetectable by users without a specialized application such as Wireshark.
The In-App Action Panel (“IAAP”) program was operational on Facebook from June 2016 until around May 2019.
“This is not a novel matter; it has been documented for years.” The plaintiffs’ allegations are without merit and entirely unrelated to the case at hand,” a spokesperson for Meta stated to Cybernews.
Meta subsequently filed a response to the plaintiffs’ petition in their own judicial document on Tuesday.
“Snapchat’s internal 30(b)(6) advertising witness has attested that the company is unable to “identify a single ad sale that [it] lost due to Meta’s use of user research products,” is unaware of whether other competitors gathered comparable information, and is unaware of whether any of Meta’s research provided a competitive advantage,” asserts Meta.
Zuckerberg’s participation
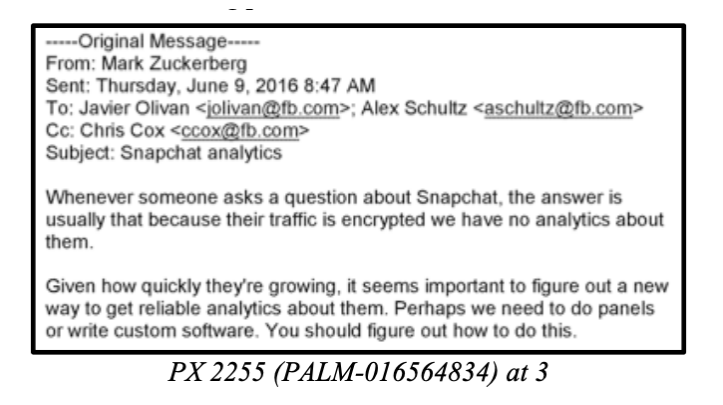
Advertisers who have filed a lawsuit against Meta assert that the covert program was initiated per Mark Zuckerberg’s request. According to internal emails sent by Zuckerberg to senior executives in June 2016, the rapid expansion of Snapchat caused him concern. Facebook was unable to obtain analytics pertaining to a competitor due to the encryption of their traffic.
“Given how rapidly they’re expanding,” Zuckerberg stated, “it seemed crucial to “figure out a new method to obtain reliable analytics about them” via panels or custom software.
Javier Olivan, the current chief operational officer of Facebook, concurred and assigned “outside the box thinking” to Onavo, a Meta acquisition of a VPN-like service in 2013, regarding this “extremely important” task.
Olivan proposed the possibility of compensating users for allowing them to “install a tremendously heavy piece of software (which could even kill a human in the middle, etc.).”
The Onavo team produced a kickoff presentation for the “Ghostbusters project” by mid-June 2016, which made use of the Snapchat ghost logo.
Plaintiffs assert that between June 2016 and early 2019, this “man-in-the-middle” strategy, which utilized a server-side SSL surge technology executed on Facebook’s Onavo servers, was in fact implemented en masse, as supported by documents and testimony.
Allegedly, in 2017 and 2018, the spyware capable of acquiring, decrypting, and transmitting the data was utilized against Amazon and YouTube, respectively.
The code contained a client-side “kit” that installed a root certificate on the mobile devices of Snapchat users. Server-side code presumably used Facebook’s servers to generate bogus digital certificates that mimicked the trusted analytics servers of the applications, thereby decrypting and redirecting analytics traffic for Facebook’s own analysis.
A Facebook strategist speculated that Snapchat’s competitive challenges were possibly attributable to the product initiatives that they provided insights on through this Onavo analysis.
Facebook’s redesigns, according to testimony from a Snap executive, hindered the company’s ability to sell advertisements.
According to Business Insider, Facebook implemented Stories on Instagram at that time, which is essentially the same as Snapchat’s primary function of erasing photo uploads.
A separate document reveals that in early 2019, Meta executives conducted a company-wide effort to analyze and convey the program’s risks and rewards to Zuckerberg so that he could personally decide whether to continue, in response to an Apple enforcement action implicating the IAAP conduct.
It is highly probable that Facebook’s covert operation contravened the Wiretap Act, a piece of legislation that explicitly forbids the unauthorized interception and use of electronic communications. Facebook intercepted and decrypted Snapchat’s traffic without the company’s consent, then utilized the data for “tortious purposes.”
A portion of Facebook staff did not endorse the Ghostbusters initiative. Pedro Canahuati, the director of security engineering, shared Jay Parikh’s apprehensions, stating, “I am unable to conceive of a convincing justification for why this is acceptable. No security personnel is ever at ease with this, regardless of the public’s approval, according to NDTV.
Invading Indian energy and defense sectors with malware masquerading as an Air Force invitation
A court document states, “The company’s highest-level engineering executives considered the IAAP Program to be a legal, technical, and security nightmare.”
The documents became public as part of a class action lawsuit against Facebook in a federal court in California. TechCrunch reported that Meta faces accusations of misleading users about its data collection practices and using “deceptively extracted” information to gain an unfair advantage.
A TechCrunch investigation revealed that Facebook had been covertly paying adolescents to use Onavo so the company could access all of their web activity. As a result, Facebook discontinued Onavo in 2019.
A man-in-the-middle (MITM) attack is a form of cyber assault wherein a malicious actor surreptitiously intercepts the communication of two entities with the intention of eavesdropping on the flow of data and potentially manipulating the transmitted information.