A novel phishing attack conceals a keylogger within a bank payment notification.
We’ve identified a recent phishing campaign that uses unique loader malware to spread Agent Tesla, an information stealer and keylogger.
On March 8, 2024, Trustwave SpiderLabs identified a phishing email containing this attack chain. The attack chain encourages the user to access an archive file attachment under the guise of a bank payment notification.
A malicious launcher is concealed within the archive (“Bank Handlowy w Warszawie-ddowód wpłaty_pdf.tar.gz”), which initiates the process to install Agent Tesla onto the compromised host.
Invading Indian energy and defense sectors with malware masquerading as an Air Force invitation
“In order to evade detection, this loader then employed obfuscation and polymorphic behavior in conjunction with complex decryption techniques,” security researcher Bernard Bautista wrote in an analysis published on Tuesday.
“The loader also exhibited the capability to bypass antivirus defenses and retrieve its payload using specific URLs, with user agents leveraging proxies to further obfuscate traffic.”
Threat actors have utilized the strategy of incorporating malware within files that appear to be harmless on numerous occasions in an attempt to deceive unsuspecting victims into initiating the infection process.
The attack implements the loader in .NET. According to Trustwave, there were two different versions of the loader. Each one used a different decryption method to get to its configuration and get the encrypted XOR payload from a remote server.
In order to avoid detection, the injector circumvents the Windows Antimalware Scan Interface (AMSI), a mechanism that allows security software to scan files, memory, and other data for potential threats.
“Patching the AmsiScanBuffer function to evade malware scanning of in-memory content” is how Bautista accomplishes this.
The final stage entails the decoding and execution of Agent Tesla in memory, which enables the malicious actors to covertly transfer confidential information through SMTP by utilizing a compromised email account linked to a reputable security system provider in Turkey (“[email protected]”).
According to Trustwave, this method not only avoids any suspicious activity but also provides an additional level of concealment that complicates the task of attributing the attack to the adversary, thereby obviating the need to establish specialized exfiltration channels.
“[The loader] employs methods like patching to bypass Antimalware Scan Interface (AMSI) detection and dynamically load payloads, ensuring stealthy execution and minimizing traces on disk,” Bautista stated. “This loader marks a notable evolution in the deployment tactics of Agent Tesla.”
BlueVoyant’s discovery of an additional phishing operation by TA544, a cybercriminal organization, coincides with the revelation. TA544 uses PDFs masquerading as legitimate invoices to spread WikiLoader, also known as WailingCrab, and establish connections with a command-and-control (C2) server, which is almost exclusively responsible for compromised WordPress sites.
Notably, in November 2023, TA544 used a Windows security bypass vulnerability called CVE-2023-36025 as a weapon to install the Remcos RAT through the IDAT Loader loader family and take control of systems that were already infected.
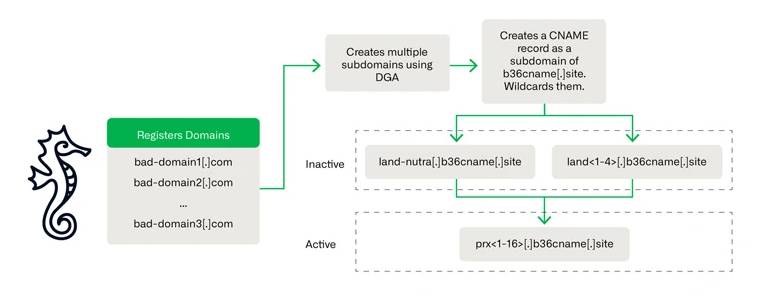
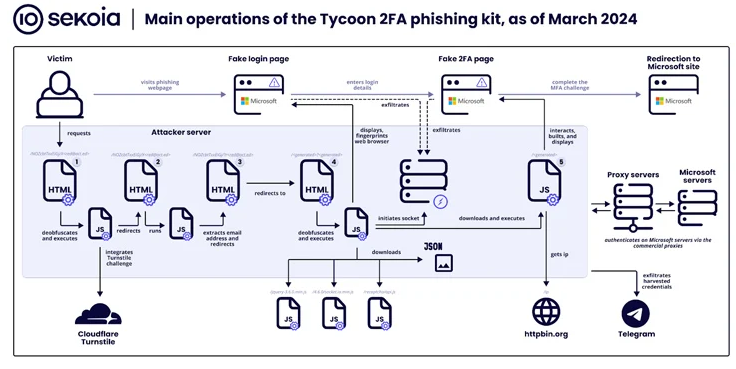
The results additionally coincide with an increase in the utilization of a phishing kit known as Tycoon, which, according to Sekoia, has “become one of the most pervasive adversary-in-the-middle phishing kits in recent months, detecting over 1,100 domain names between late October 2023 and late February 2024.”
Trustwave exposed Tycoon last month; it enables cybercriminals to impersonate Microsoft 365 users in order to obtain their credentials, session cookies, and two-factor authentication (2FA) codes via bogus login pages. Reports indicate that Tycoon has been operational since at least August 2023, offering its services through private Telegram channels.
The phishing kit’s extensive traffic filtering methods thwart phishing attempts by requiring site visitors to complete a Cloudflare Turnstile challenge before redirecting them to a page that harvests credentials.
A critical, unpatched vulnerability in the Ray AI platform was exploited to mine cryptocurrencies.
Additionally, operational and aesthetic resemblances between Tycoon and the Dadsec OTT phishing kit suggest that the developers may have accessed and modified the Dadsec OTT phishing kit’s source code to suit their purposes. The revelation of the Dadsec OTT source code in October 2023 substantiates this assertion.
“The developer enhanced stealth capabilities in the most recent version of the phishing kit,” Sekoia reported. “Recent updates may reduce the rate at which security products detect the Tycoon 2FA phishing pages and the underlying infrastructure.” Furthermore, its affordability and user-friendliness contribute to its widespread adoption among malicious actors.