
Magnet Goblin Hacker Group Uses One-Day Exploits to Deploy Nerbian RAT
Magnet Goblin, a financially driven threat actor, is quickly adding one-day security vulnerabilities to its arsenal in order to exploit edge devices and public-facing services and spread malware on affected systems.
“Threat actor group Magnet Goblin’s hallmark is its ability to swiftly leverage newly disclosed vulnerabilities, particularly targeting public-facing servers and edge devices,” Check Point stated in a statement.
“In some cases, the deployment of the exploits is within 1 day after a [proof-of-concept] is published, significantly increasing the threat level posed by this actor.”
Password pirates are targeting PetSmart accounts.
Attacks launched by the adversary have used unpatched Ivanti Connect Secure VPN, Magento, Qlik Sense, and maybe Apache ActiveMQ servers as an initial infection vector to obtain unauthorized access. The gang is claimed to have been operating since at least January 2022.
Following a successful exploitation, a cross-platform remote access trojan (RAT) known as Nerbian RAT, initially reported by Proofpoint in May 2022, and its simplified variation, MiniNerbian, are deployed. Darktrace previously exposed the usage of the Linux version of the Nerbian RAT.
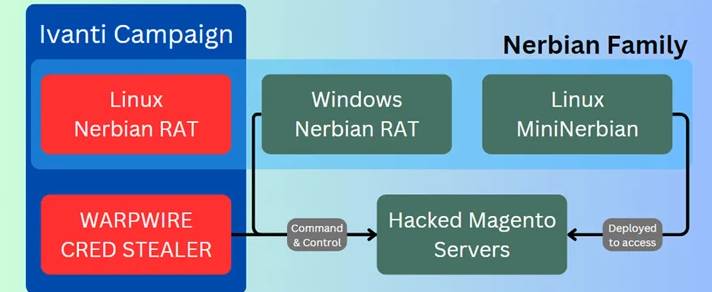
Both strains enable the execution of arbitrary orders received from a command-and-control (C2) server, as well as the exfiltration of backed-up results.
Magnet Goblin also use the WARPWIRE JavaScript credential stealer, the Go-based tunneling program Ligolo, and genuine remote desktop applications such as AnyDesk and ScreenConnect.
Apple will not update third-party applications if customers leave the EU.
“Magnet Goblin, whose campaigns appear to be financially motivated, has been quick to adopt 1-day vulnerabilities to deliver their custom Linux malware, Nerbian RAT and MiniNerbian,” the business stated in a statement.
“Because they are mostly found on edge devices, these tools have largely escaped notice. This is part of a continuing trend among threat actors to target previously vulnerable locations.”

