Cybercriminals are using a novel technique called DNS hijacking to commit investment scams.
Savvy Seahorse, a new DNS threat actor, is using cunning tactics to lure victims into fraudulent investment platforms so they may steal money.
“Savvy Seahorse is a DNS threat actor who convinces victims to create accounts on fake investment platforms, make deposits to a personal account, and then transfers those deposits to a bank in Russia,” according to a study released last week by Infoblox.
Russian, Polish, Italian, German, Czech, Turkish, French, Spanish, and English speakers are among the targets of the operations, suggesting that the threat actors are broadening their scope when launching their assaults.
Users are tricked into parting with their personal information in exchange for purportedly high-return investment possibilities using fraudulent ChatGPT and WhatsApp bots, in addition to being seduced by adverts on social networking sites like Facebook.
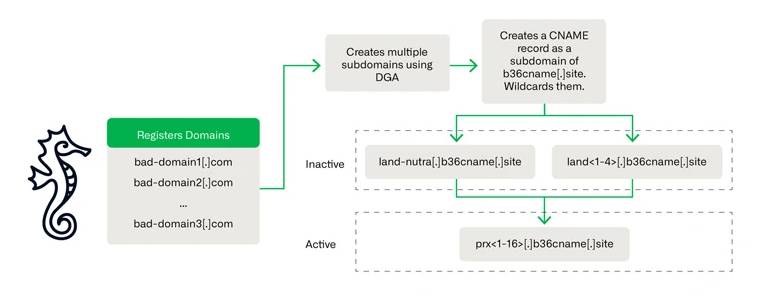
The use of DNS canonical name (CNAME) records to establish a traffic distribution system (TDS) in financial scam campaigns is noteworthy since it has enabled threat actors to avoid detection since at least August 2021.
Rather of linking to an IP address, a CNAME record maps a domain or subdomain to another domain (i.e., an alias). This method has the benefit that just the DNS A record for the root domain has to be changed when the host’s IP address changes.
Astute Seahorse takes advantage of this method by establishing many temporary subdomains that are connected via a shared CNAME record, and therefore, an IP address. These particular subdomains are linked to the main campaign domain and are generated using a domain generating algorithm (DGA).
The infrastructure is immune to takedown attempts since the domains and IP addresses are dynamic, enabling threat actors to regularly register new domains or change their CNAME records to a new IP address when their phishing sites are taken down.
Although threat actors like as VexTrio have used DNS as a TDS, this revelation is the first instance of CNAME records being utilized in this way.
When victims click on the links hidden in Facebook adverts, they are asked to provide their phone number, email address, and name. They are then sent to a fake trading platform where they may add money to their wallets.
“An important detail to note is the actor validates the user’s information to exclude traffic from a predefined list of countries, including Ukraine, India, Fiji, Tonga, Zambia, Afghanistan, and Moldova, although their reasoning for choosing these specific countries is unclear,” said Infoblox.
This discovery coincides with the disclosure by Guardio Labs that thousands of domains associated with reputable companies and organizations have been taken over and used to spread spam campaigns using a process known as CNAME takeover.








