
How Indian UPI is Being Used by Cybercriminals for Money Laundering Operations
Cybercriminals are using an Android-based application to manage a vast money laundering scam via a network of hired money mules in India.
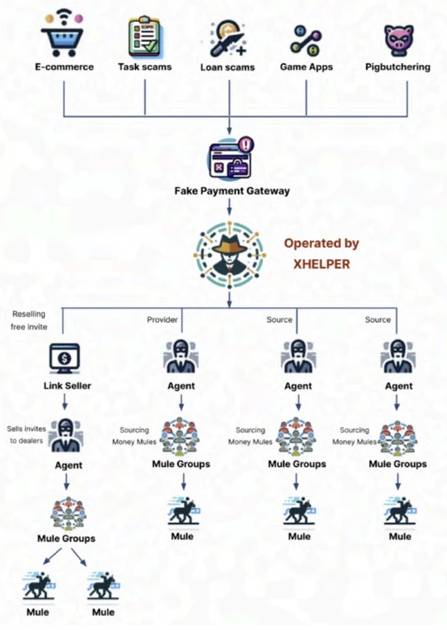
The malicious program, known as XHelper, is a “critical instrument for onboarding and overseeing these money mules,” according to a paper by CloudSEK researchers Santripti Bhujel, Abhishek Mathew, and Sparsh Kulshrestha.
The first information about the scam surfaced in late October 2023, when it was discovered that Chinese cybercriminals were using the fact that Indian Unified Payments Interface (UPI) service providers are exempt from the Prevention of Money Laundering Act (PMLA) to start illicit transactions while pretending to be offering an instant loan.
Hired mules are people who are recruited via Telegram in exchange for fees that range from 1% to 2% of the total transaction amounts. The illicit gains from the activity are then transferred to these mules’ other accounts.
The cybersecurity group said at the time that “Chinese payment gateways are central to this operation because they are precisely exploiting the UPI QR code feature.”
“The scheme leveraged a network exceeding hundreds of thousands of compromised ‘money mule’ accounts to funnel illicit funds through fraudulent payment channels, ultimately transferring them back to China.”
XHelper, which allows the technology underlying fraudulent payment gateways used in pig slaughtering and other frauds, is an effective method to handle these mules. The application is disseminated via websites that pose as reputable companies and go under the name “Money Transfer Business.”
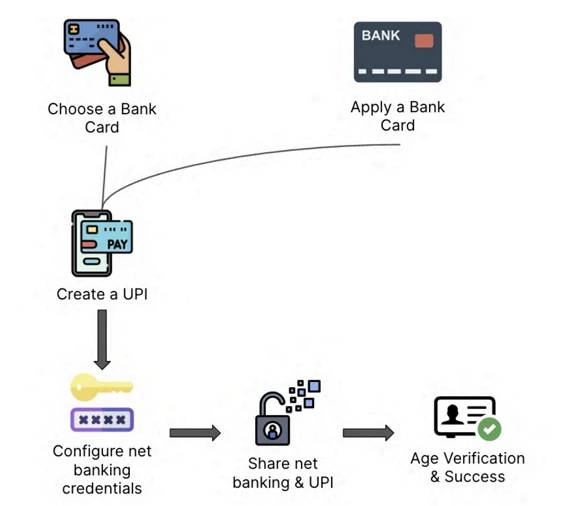
The application further provides mules with the option to monitor their profits and optimize the whole payment and collection procedure. They must first complete an initial setup procedure where they must create their online banking credentials and register their unique UPI IDs in a certain manner.
Payouts require money to be sent to pre-designated accounts within 10 minutes, while collection orders are more passive; money is sent to the registered accounts from other fraudsters using the network.
“Money mules activate order intake within the XHelper app, enabling them to receive and fulfill money laundering tasks,” according to the investigators. “The system automatically assigns orders, potentially based on predetermined criteria or mule profiles.”
In order to encourage continuous involvement, mules are required to provide screenshots of the unlawful cash transfer after it has been completed using the associated bank account. These images are authenticated and then submitted for payment.
One of XHelper’s features is the ability to invite other people to become agents, who are in charge of finding mules to join. They may get incentives for each new recruit via a referral system, which leads to an ever-growing network of agents and mules.
“This referral system follows a pyramid-like structure, fueling mass recruitment of both agents and money mules, amplifying the reach of illicit activities,” the investigators said. “Agents, in turn, recruit more mules and invite additional agents, perpetuating the growth of this interconnected network.”
Using a Learning Management System (LMS) that provides training on creating fictitious corporate bank accounts (which have larger transaction limits), the various processes, and methods to earn more commission, XHelper also helps teach mules to effectively launder stolen assets.
In addition to preferring the UPI function included in reputable banking applications for carrying out the transactions, the platform serves as a central location for figuring out how to evade account freezes so that mules may go on with their illicit operations. Additionally, they get instruction on how to respond to bank customer service inquiries about questionable transactions.
“While XHelper serves as a concerning example, it’s crucial to recognize this isn’t an isolated incident,” CloudSEK said, adding that it has uncovered a “growing ecosystem of similar applications facilitating money laundering across various scams.”
Europol said in December 2023 that 1,013 people had been taken into custody during the second half of 2023 as a result of an international campaign to combat money laundering. In addition, 10,759 money mules and 474 recruiters (also known as herders) were identified as a result of the multinational law enforcement investigation.
The revelation coincides with Kaspersky’s revelation that, from February 2023 until the end of the year, mobile device malware, adware, and riskware assaults increased rapidly.
“Android malware and riskware activity surged in 2023 after two years of relative calm, returning to early 2021 levels by the end of the year,” the security company in Russia said. “Adware accounted for the majority of threats detected in 2023.”








