Exit Scam: After receiving $22 million in payments, the BlackCat ransomware group disappears
Following the posting of a false law enforcement seizure banner, the threat actors responsible for the BlackCat ransomware shut down their darknet website and most likely performed an escape fraud.
“BlackCat/ALPHV was not apprehended. The security researcher Fabian Wosar said, “They are exit scamming their affiliates.” “It is blatantly obvious when you check the source code of the new takedown notice.”
“There is absolutely zero reason why law enforcement would just put a saved version of the takedown notice up during a seizure instead of the original takedown notice.”
The National Crime Agency (NCA) of the United Kingdom informed Reuters that it was unrelated to any outages to the BlackCat network.
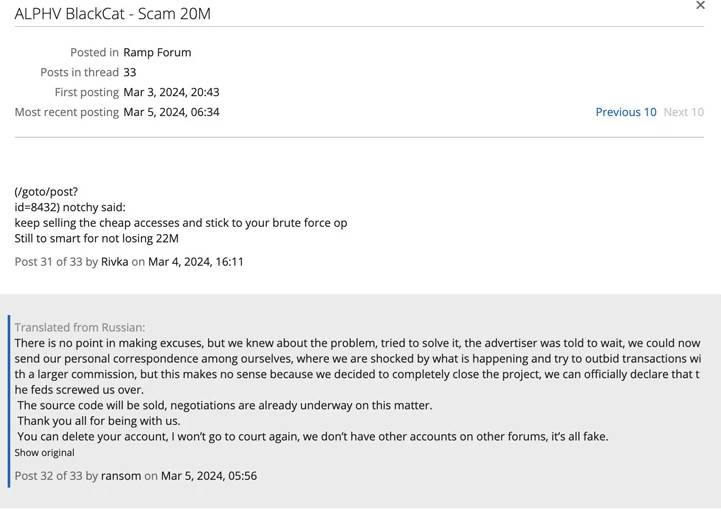
Noted On the social networking platform X, future security researcher Dmitry Smilyanets shared photos of BlackCat actors claiming the “feds screwed us over” and said they planned to sell the ransomware’s source code for $5 million.
It reportedly accepted a $22 million ransom payment from UnitedHealth’s Change Healthcare business (Optum) and declined to provide the money to an affiliate that had carried out the assault, which is why it went missing.
The business has said it is solely focusing on the incident’s investigation and recovery, declining to comment on the reported ransom payment.
The unhappy affiliate, whose account was terminated by administrative staff, allegedly made the accusations on the RAMP cybercrime forum, according to DataBreaches. “They emptied the wallet and took all the money,” they said.
This has sparked rumors that BlackCat organized an exit fraud in order to avoid detection and later reappear under a different name. A now-former admin of the ransomware organization was cited as stating, “A re-branding is pending.”
In December 2023, law enforcement confiscated BlackCat’s infrastructure; nevertheless, the cybercriminal group was able to retake control of their servers and resume operations with few repercussions. Previously, the organization went under the names DarkSide and BlackMatter.
According to DomainTools security analyst Malachi Walker, “BlackCat may be concerned about moles within their group internally, and closing up shop preemptively could stop a takedown before it occurs.”
Conversely, this exit scam may just be BlackCat’s way of making off with the money. As cryptocurrencies are at an all-time high once again, the gang can profitably market their product as “high.” Reputation is crucial in the realm of cybercrime, and BlackCat seems to be destroying relationships with its affiliates by acting in this way.”
The malware research organization VX-Underground revealed that the LockBit ransomware operation no longer supports Lockbit Red (also known as Lockbit 2.0) and StealBit, a customized tool used by the threat actor for data exfiltration. This information coincides with the group’s apparent death and the abandonment of its infrastructure.
Following a months-long investigation and a concerted law enforcement operation that brought down its infrastructure last month, LockBit has also attempted to salvage face by shifting part of its operations to a new dark web domain.
Additionally, Trend Micro said that since its discovery in April 2023, the ransomware family known as RA World (previously RA Group) has effectively penetrated insurance, banking, and healthcare organizations throughout the United States, Germany, India, Taiwan, and other nations.
According to the cybersecurity company, the group’s attacks “involve multi-stage components designed to ensure maximum impact and success in the group’s operations.”